Hello there!
This page is about what i found in the UltaVPN client and its traffic.
First of all, what tf is "ulta"?
Welp, let's learn.
- Ulta is a program that allows people from russia to bypass the Discord ban. Is closed source, ofc.
Sounds harmless, right?
But if it was harmless, i wouldn't be writing this...
Software i used:
Ghidra, curl, wireshark, sandboxes (any.run, hybrid analysis)
Findings:
- suspicious domain hardcoded - ksfcsdf.khpkadmig.click
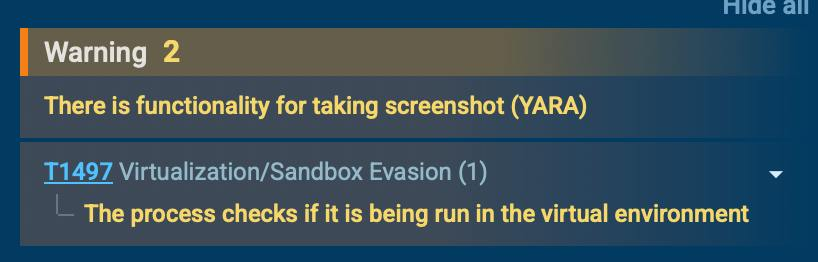
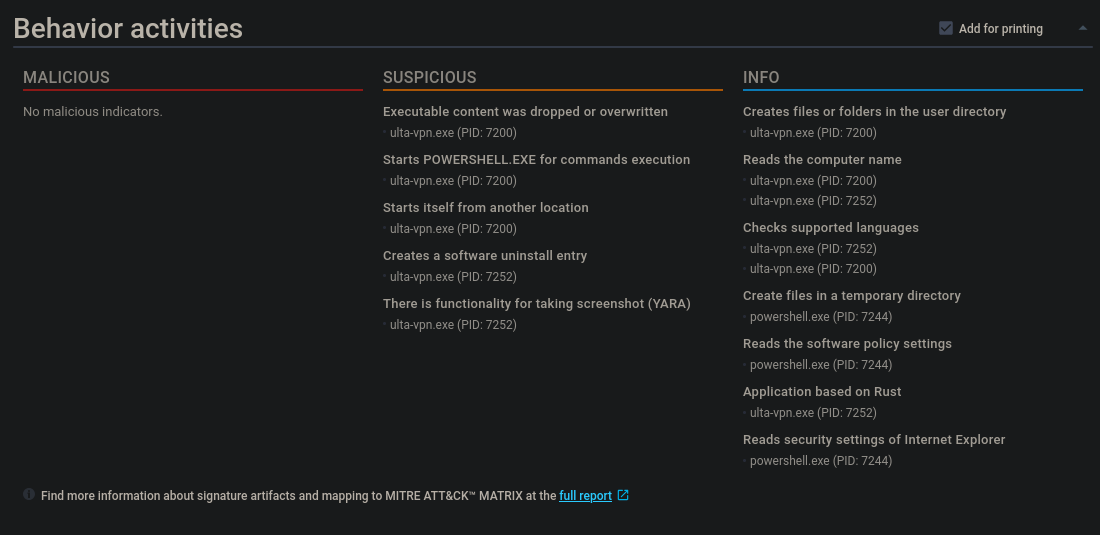
- functionality of taking screenshots (!)
- process checks if it is being run in the VM/Sandbox or being reversed (!)
- weak SSH server protection; uses ecdh-sha2-nistp256/384/521, hmac-sha1 - outdated shit with backdoors
- domain responds with 404 (but alive and configured)
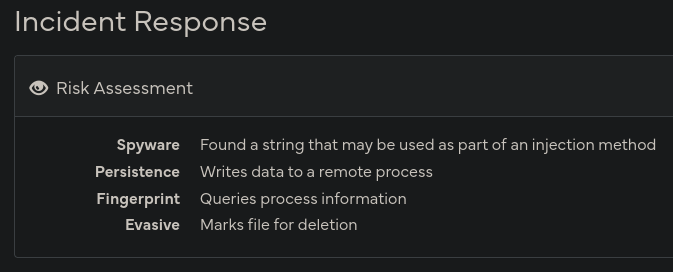
possibledata exfiltration- writes to the powershell startup profile data
- uses amneziawg
More info:
The domain thing
-----
WHOIS says that it was registered with namecheap.com and not much before the release date - december 2024
WHOIS fully - *pastebin*
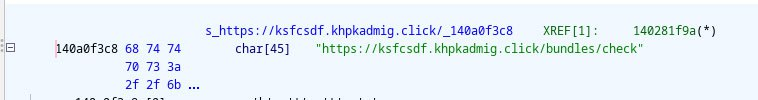
curl -v "https://ksfcsdf.khpkadmig.click/bundles/check" says that the server is alive and configured, but returns 404:
{"message":"Cannot GET /bundles/check","error":"Not Found","statusCode":404}%
the support is not responding. and yeah, i did wait. i waited for 2 months (they still didn't reply xD)
ACTUAL spyware
-----
First of all, it has functionality of taking screenshots. Do i even need to say it?
Also...
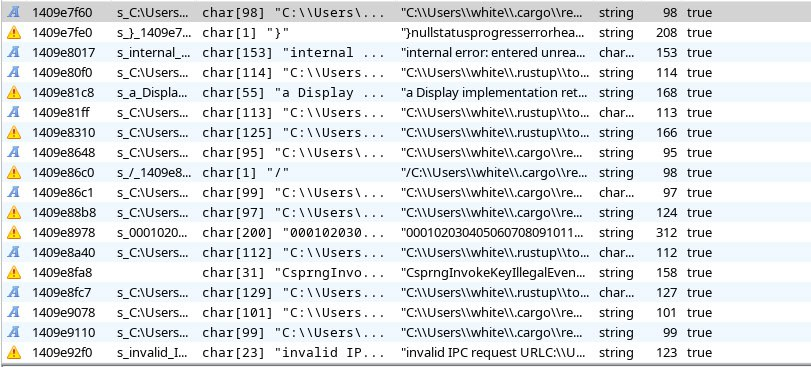
BONUS: debug garbage right in the production build!